Configure Your Galaxy Instance as an OIDC Client for your organization's Okta Infrastructure
This page explains how to configure this feature, for user-specific docs, please refer to this page.
Leveraging OpenID Connect (OIDC) protocol, users can login to Galaxy using their identity on Okta Infrastructure (AAI), without having to (explicitly) create a Galaxy user account. To enable this feature on your Galaxy instance, you would need to first register you Galaxy instance as an OIDC relying party (RP, or client) with your organization's Okta, and then use your registration information to configure Galaxy. These steps are described in details in the following sections.
Client Registration
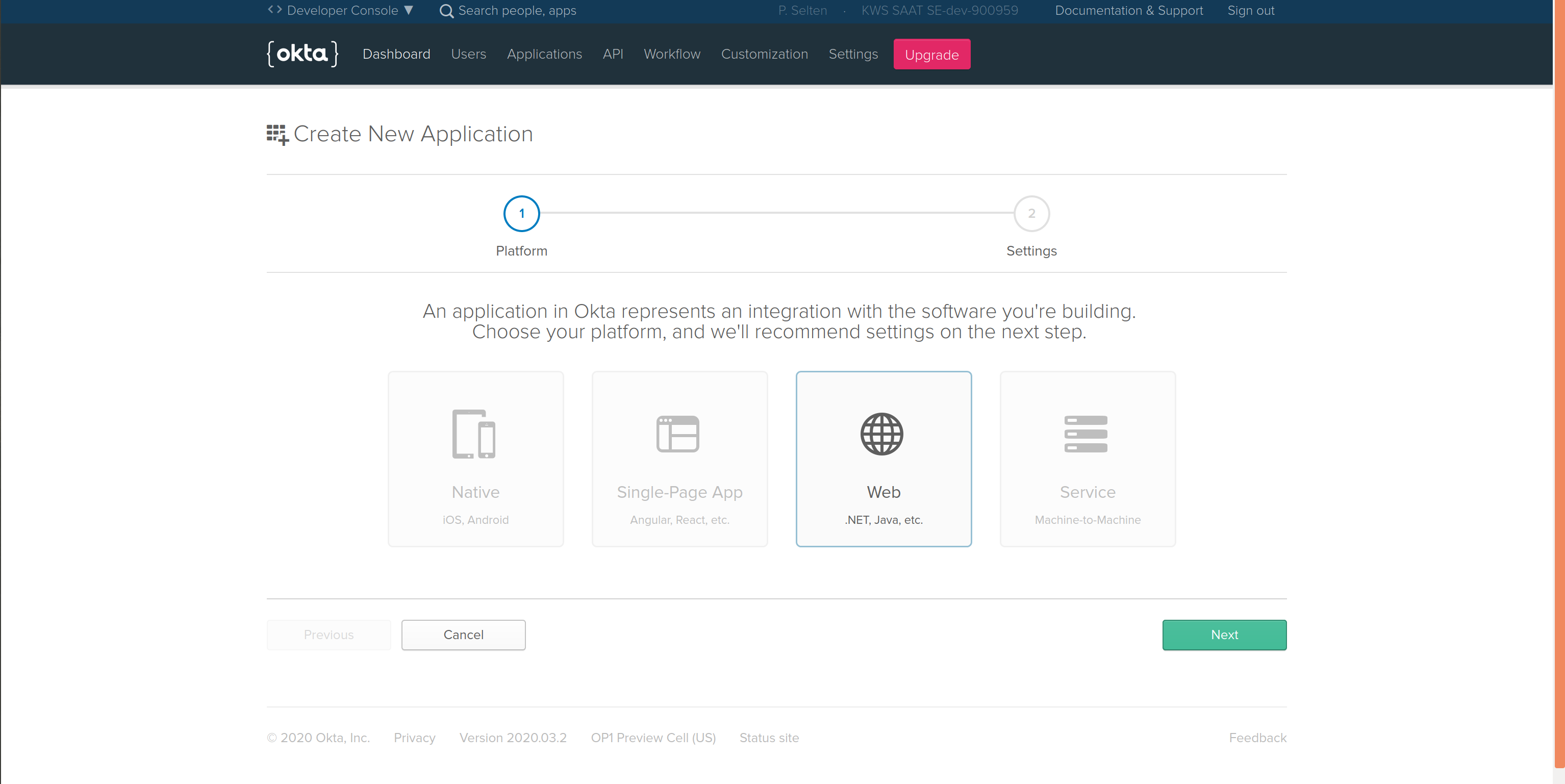
Take the following steps to register your Galaxy instance (RP) to an Okta dev environment:
- Create a Okta developer account, if you do not already have it.
-
Login to your Okta developer account's admin panel and register a new application.
' width='2560' height='1283' xlink:href='data:image/png%3bbase64%2ciVBORw0KGgoAAAANSUhEUgAAAEAAAAAgCAIAAAAt/%2bnTAAAACXBIWXMAAAsTAAALEwEAmpwYAAAF4klEQVRYhdVX229URRjvm8T4YOhtoWwBe29pubTdS7ftblsLiVGElkVbKok%2bEBJffPHF%2bCeoDzwhiHIpsWxbNDGaKDHGBzGaRqyYYGM1gQT2cu475%2bw5M3Nm1pwz28P2tjfaBn/9ejI7Zy7fb77vm%2b87ZdX%2bkUr/iRxS5R%2bt9I/u7D25KzhW0/%2b6OzRW1ROuG37DHRpzB8fdoXHWX%2bEbqfCNVvhGy72scYI1qnvCrsDJcu9IdSBc3hfe1juyLTDyXO9oTf9rO/pOVvhG3cHx2oHx3YOnagfGa0PjewYnXIHwruDY7oFTrkC4Yh2tXD3hZzuPn33rTFl9d19dV/%2ba8kJnf6Mn5DtybHh0wnv41fruYHvf4X29wy3%2boUZPqNk32OAJtviHWnuGmn2DjZ5Qk3egyTvQFniR/WzxDzFp6A62%2bYf2%2bgde6jxyznPqnHfi3c6RvV3r7ltXgDR0B10dPe%2bcHiurbDxQ3rC2bK/fX93c6Rk%2b%2bvLYm74jx8sbDuw5GNhzMFDT7q1u7ty5z1PVfMjd4dvV7t3R1lXV3Olq7XK1drk7/Dtau6uaD9W0e2vaPTXt3sqmQ%2b593u0d3Ufr%2br5rmfi2/fSHda88X79/vX0Lkaqmg8/Utp0JHyv79PrU9ekvJiM315MrUzOXJqcufz49Gbl5dWrmytTMtRuz1yKz9vPm1RuzTK4tSaYdyfRfzRp2JTJ7MTJ98cb0pchMjh0nC5DrkdnLkS9/nPqsDCGUzglCzPRTCErS6TT%2b925ZMpkkhJhrgRCS0rSFhQWO56PRaILj4vF4gkskOC766FE8Ho/FYhzPY4zNrQdGZjpt/H2nTNO03FSJDUopoTRNM2A9lNK007U5SOe0APpnPj8BZ6HV6xJKgWHm2CXvymTpIDaRwNrT7WcSmvd4XYVmmhLL4YoE84VcWubS4MkIMKgGvC8AA%2bHSHAlCmEqlCCFbTcCxrqaqksgbhrHCwQpEMpnked4wYLajFk8gVVAM5PbL1Z3rabNWPy1qr5UEUvkIrAawwfOcJEmiKGqaBgAQBEFRFEmSZFkWRVFVVUVRZGuE9ZcEgA0GKpAlSRBERVEASEqynEwCSRIFUWSWLBRPQoDFnyzLiUQiHotJtsYcx0WjUZ7nrXaCEy2VRIHnY7E4z1k/BYFPxOM8lxAEQbI4CDzPiaIYi8UBAKaJMcalEUgVpX22WZmVV12FK29GbBJsEoRNhE2ITWTlSLpierrYMCiNAKXUSdLZ%2bdsxC7sWnTYhREdmCiIdIgNhiE3dgDpEqg7XW4oWyKE0F7KO0y4cdF0HADhFhKMNxhgAkEqlsghgBCExTUVREom4NQKhlA7J0hSEEAAAQrh1BAghkiRxHOfUUQ4BCOGDBw9isVg2AQit875169b58x9rmmaapqYbxF6KUqooyvz8vCAIbPGiCRSVBxwCAABZljVNW0bAbiuKoqoq63cIEEIWFxfn5uYghBghLWMBbA3Q9YcPH7IpW0SA2V3X9RUuBA0LyAZrOAQwtp6plM7eastdCNso0YVKI2AYBlBVwzCyA9cwDE1VNU1T7Sc7eCsGEEQICYIQjUYt2lkEMMa6rquqquv6FhFg2xiGoVv/GSPQLG3sbp0FpfVFAS31gaoKgigriiTLBoTAjoHMOktTdN3YdALZnwdr3OLLEwJ7hQnRIbKvfwLtPGAgbCCc9XHxGJmV7eqCycYT2FQQShEleElMW8snJfD4iyyrjmcH5qShjQItIRPnJcCcm90V7NJgqYdln%2bIKmPVBbNV/Tdw/%2b3Pkvd%2b%2bfv/ON2//MnNh4bZdrNLcBNQ8S9tH7gQrQghCqKpqMplkd%2bUGErgnxT64%2b/2Fv376ZOH2R3/%2b8NX9u8uq7dIIPKWgJRFwfDSvs7IgyW4XAkIItsW0I5iZZWNigLkQK2BY7FoNnHllu9njOGE9zixaPMwlp81H4I%2bCCLDAZYUKU8sOBqvBXlGaiROmM4RWEcEm5lIinXNTiHBeAou//39jwPIuJHP/ATYcm93smGwcAAAAAElFTkSuQmCC' /%3e%3c/svg%3e)
- Set the "Base URI", "Login redirect URIs", "Logout redirect URIs", "Group assignments" and "Grant type allowed.
- Click the green "Done" button at the bottom and make a note of all
the generated credentials that is made available to you. The
Client IDandClient Secretfields will be used to configure Galaxy, andClient Configuration URLandRegistration Access Tokenwill be needed to access the client registration in future. - Use the returned information to setup Galaxy to receive authentication requests using Okta!
Galaxy Configuration
You would need to setup your Galaxy instance to leverage OIDC protocol.
This setup is common for all OIDC IdPs, and is
documented at this page.
Then you would need to add Okta-specific setters to the config/oidc_backends_config.xml
matching the values you got from the client registration process, as well as the exact same
redirect_uri you specified (depending on your setup):
<?xml version="1.0"?>
<OIDC>
<provider name="Okta">
<client_id> ... </client_id>
<client_secret> ... </client_secret>
<redirect_uri>http://localhost:8080/authnz/okta/callback</redirect_uri>
<api_url>https://organization.okta.com/oauth2</api_url>
</provider>
</OIDC>
Having set this configuration, restart Galaxy to have the option of login to Galaxy with your organization's Okta identity: